Written by Nicholas Howland on 11/21/2024
MetaCTF November 2024 CTF
MetaCTF is a CTF platform which offers monthly CTF's as well as a Cyber Range which has hundreds of capture the flag challenges in all areas. The website can be found here: https://metactf.com/
Writeup
There were 5 challenges covering Binary Exploitation, Cryptography, Forensics, Reverse Engineering, and Web Exploitation. I was able to complete 3/5 in the two hours coming in at 26th place out of 896 participants.
Challenge: Slithering Security
Prompt:
Help me test my sssecurity, can you get the flag from this ssssecure sssscript?
Challenge code:
#!/usr/bin/env python3
SECRET_FLAG=b"\x54\x57\x56\x30\x59\x55\x4e\x55\x52\x6e\x74\x6b\x4d\x47\x34\x33\x58\x7a\x64\x79\x64\x58\x4d\x33\x58\x32\x4e\x73\x4d\x57\x34\x33\x63\x31\x39\x33\x61\x54\x64\x6f\x58\x33\x4d\x7a\x59\x33\x49\x7a\x4e\x33\x4e\x7a\x63\x33\x4e\x7a\x63\x33\x4e\x39"
HASHED_PASSWORD = b'\x12\x1eW\x98\x00\xc1C\xff\xe3\xa9\x15\xde\xd9\x00\x9b\xc9'
from base64 import b64decode
from hashlib import md5
def check_password(password):
m = md5()
m.update(password)
return m.digest() == HASHED_PASSWORD
def main():
while True:
inp = input("Please enter your passssssword: ").encode()
if check_password(inp):
print(f"Well done, your flag isssssss {b64decode(SECRET_FLAG).decode()}")
exit()
else:
print("Passsssssword incorrect, please try again.")
if __name__ == "__main__":
main()
Solution:
- This python script is a super simple password protection script that hides the SECRET_FLAG variable behind a simple password check.
- This can be easily defeated by taking the value of the SECRET_FLAG and decode its hex value to reveal the flag
MetaCTF{d0n7_7rus7_cl1n7s_wi7h_s3cr37sssssss}
Challenge: Admin Portal
Prompt
I'm writing a webpage for admins to check on their flags, can you do me a favor and check it out to make sure there aren't any issues?
Solution
- The link provided leads to a webpage that displays the following:
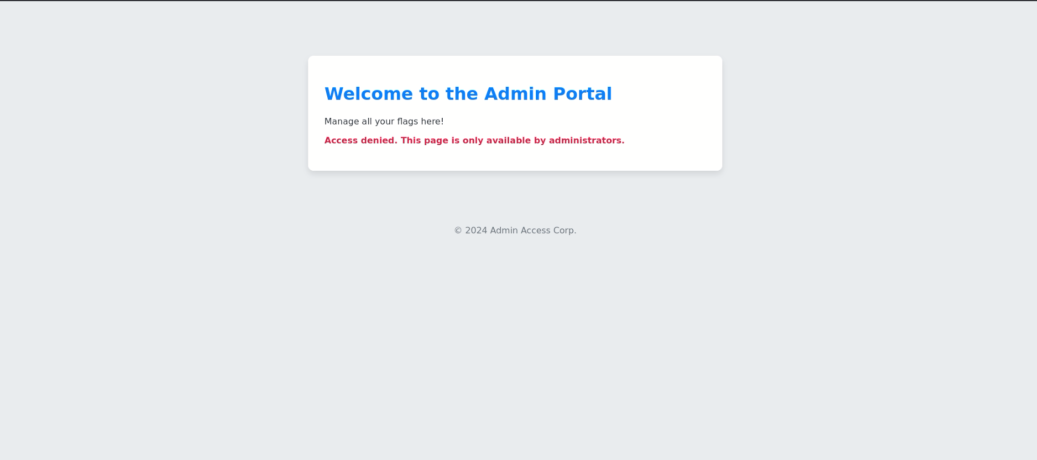
- First I opened up ZAP Proxy and took a look at what the request was doing.
- Then tried to find a robots.txt file to see if there were any pages that were disallowed from the robots.txt file, nothing.
- Next I took a look at the requests and responses in ZAP The first thing I spotted was a role cookie with a plaintext key of user
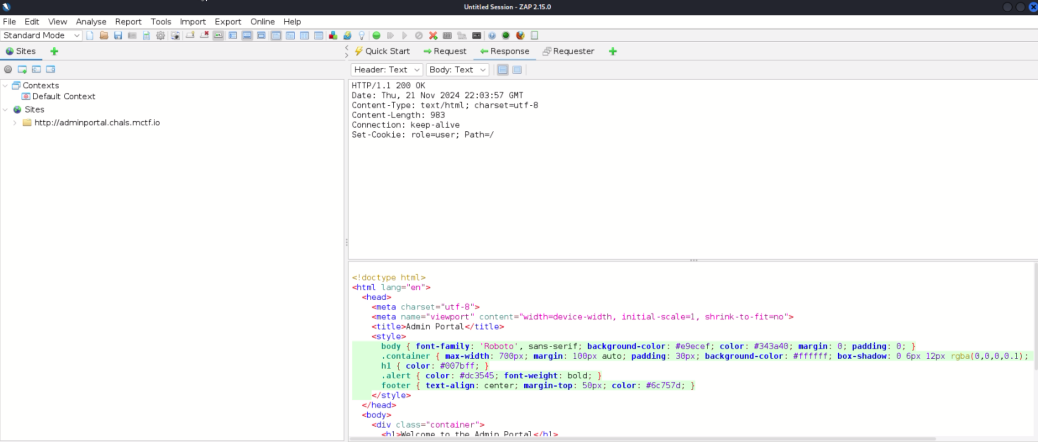
- By changing the cookie value to be admin the flag was revealed
MetaCTF{co0ki3_p0wer3d_p0rt4l}
Challenge: Talk To Me
Prompt
We managed to tap the headphones of a member of a prolific cyber actor group. Can you listen to their secret plan?
Solution
- This one had me stumped for a while and the following is not a complete list of steps and troubleshooting that was done to reveal the final audio file product.
- First I took a look at the data in the USB packet capture and noted that there was only one USB device.
- Next the packet data was exported into a JSON file
- Then the file was grepped for the USB datagrams and dropped into a plaintext file
- Then the plaintext file was fed to CyberChef and output as a raw datafile.
- Next Audacity was used to open the file as a raw data stream and downloaded as a mp3 file.
- Upon playing the MP3 file the flag was revealed by spoken word, I got it wrong a couple of times but eventually got it. metactf{4_l1ttl3_b1rd_t0ld_m3}
Failed Challenges but Good lessons
Challenge: Steg64
Prompt
You've heard of Base64, but I present to you Steg64! Challenge Code
VEh=
QT==
Tl==
S5==
IF==
Wd==
Tx==
VY==
IF==
SA==
Qd==
Q1==
Sx==
RR==
Up==
Ie==
Cs==
Ct==
Qh==
VX==
VN==
IJ==
T4==
Vc==
Ut==
IN==
Rt==
TH==
Qc==
R8==
IN==
Se==
Ux==
IN==
SR==
Ts==
II==
Qd==
Th==
T3==
VN==
SI==
RY==
Us==
IF==
Q9==
QQ==
U9==
VF==
TP==
RU==
IQ==
Notes
- So this data when decoded will end up showing the following message:
THANK YOU HACKER!
BUT OUR FLAG IS IN ANOTHER CASTLE!
- When changing CyberChef filter to not filter non printing characters there is some extra data shown
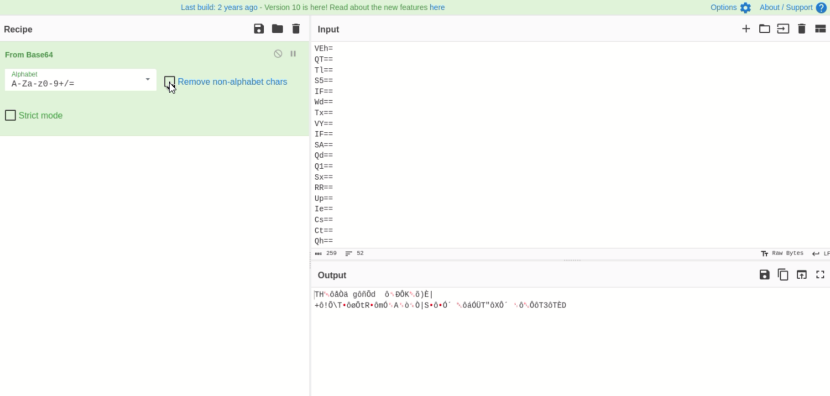
- I was running out of time here and ended up blindly trying to remove the trailing and preceding letters in each line to see if that would work. Unfortunately it did not but I was at the begining of the path to finding the answer. I am not an advanced base64 magic user. The Full Writeup from MetaCTF: https://metactf.com/blog/flash-ctf-steg64/ Another Helpful link to understanding what was going on here: https://hexarcana.ch/b/2024-08-16-base64-beyond-encoding/
Challenge: Pikalang
Prompt
I just heard about this cool new esoteric programming language called Pikalang!
It has no silly strcpy()'s or heaps, so it must be super effective against hackers.
Notes
- I did not see that the interpreter was available for download which really kneecapped my testing process.
- Pikalang is a joke programming language that uses syntax based off of Pikachu noises.
- I did my usual thing of trying to read out of bounds in either direction from the interpreters starting memory location which was not successful.
- This actually ended up relying on breaking the executable in order to get a shell to the docker container and then printing the flag out from there.
Full MetaCTF writeup here: https://metactf.com/blog/flash-ctf-pikalang/