SharePoint Scramble

Image generated by OLLAMA and Article Written by Nicholas Howland on July 23rd 2025
Updated 7/31/2025 - added some thoughts
On to the News of the Day: Widespread SharePoint Exploitation
The Cybersecurity and Infrastructure Security Agency aka CISA released an update to their advisory on a SharePoint vulnerability that uses CVE-2025-49704 and CVE-2025-49706 which allow for the execution of code over the network on July 22, 2025 (CISA SharePoint). This alert was released in light of a Microsoft threat intelligence report that detailed the release of patches for these vulnerabilities. According to Microsoft "Microsoft has observed two named Chinese nation-state actors, Linen Typhoon and Violet Typhoon exploiting these vulnerabilities targeting internet-facing SharePoint servers." as well as another Chinese based threat actor Storm-2603 actively exploiting the vulnerability, however they were only willing to assign medium confidence to the last APT the being directly attributed to a Chinese state backed threat group because of activity linked to ransomware in the past (Microsoft Threat Intelligence). The CVE-2025-53770 is ranked at a 9.8 and allows for unauthenticated attackers to send serialized data to a server and execute code over the network. CVE-2025-49704 scores 8.8 or high on the CVSSS score allowing for code injection over the network with low code complexity. The attack targets on premise Microsoft SharePoint Enterprise Server 2016 and 2019, cloud/office 365 instances are not affected. Side note: The use of Ransomware and crypto related cybercrime is more indicative of North Korean state backed hacking groups aka the Lazarus Group.
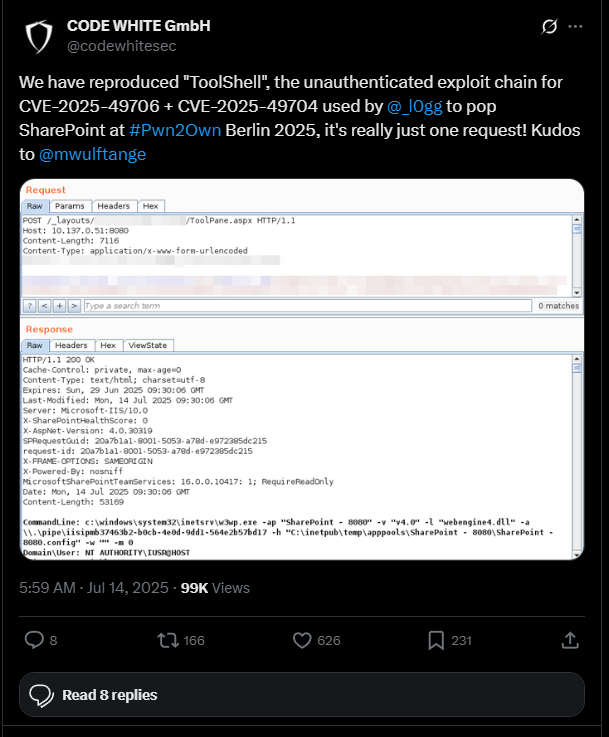
This vulnerability was actually first exhibited at the Pwn2Own competition in Berlin this May, 2025. (Goodin, ArsTechnica) According to Eye Security, who claims to be the first in detecting the large scale active exploitation and is attributed in much of the reporting because of the stellar research post they published. The team at Eye security preformed scans on over 23000 SharePoint servers and discovered 400 active compromises as of July 23rd 2025. Three days before active exploitation an offensive security team Code White GmbH demonstrated the capability to reproduce the unauthenticated RCE on SharePoint servers https://x.com/codewhitesec/status/1944743478350557232 (Eye Security). Eye security was scanning the internet for systems that were already infected by the exploit and working to notify companies (Eye Security). this is the way of ethical hacking and security research, disclosing vulnerabilities on servers that have reached their end of service date and are no longer supported or recieving patches.
Eye Security also provided a handy bash script checks to find hosts that have been infected
# determine SharePoint version
curl -s -I -X OPTIONS --connect-timeout 5 "https://$HOST" \
| grep -i "^MicrosoftSharePointTeamServices:" \
| awk '{print $2}' | tr -d '\r'
# fetch malicious aspx endpoint (note that SP always returns HTTP 200 even if file does not exist)
RESPONSE=$(curl -s -w "HTTPSTATUS:%{http_code}" --connect-timeout 5 "$URL")
BODY=$(echo "$RESPONSE" | sed -e 's/HTTPSTATUS\:.*//g')
STATUS=$(echo "$RESPONSE" | tr -d '\n' | sed -e 's/.*HTTPSTATUS://')
SIZE=$(echo -n "$BODY" | wc -c)
# filter on HTTP response bodies of exactly 160 bytes in size
if [ "$STATUS" = "200" ] && [ "$SIZE" -le 160 ]; then
echo "$BODY"
fi
# if the aspx implant is there, you now have obtained proof (160 bytes long)
# response body format (example):
[A-Z0-9]{64}|HMACSHA256|[A-Z0-9]{64}|Auto|Framework20SP1
According to the Microsoft Threat intelligence post. The attackers send a POST request to a vulnerable server to the /ToolPane.aspx uri. Once successfully exploited the attackers will usually deploy a web shell to dig in further. The filenames of these shells have been observed as variants of spinstall.aspx or spinstall0.aspx. These aspx scripts retrieve MachineKey data, which is responsible for hashing and encryption settings for application services as well as keys more about machine keys can be found in the Microsoft documentation here: https://learn.microsoft.com/en-us/purview/sit-defn-asp-net-machine-key. The results are returned through a GET request to the C2 server. Microsoft observed the threat actors actively exploiting this vulnerability on July 7, 2025.
Palo Alto also released a Threat Brief on the SharePoint vulnerability on July 22, 2025 (Unit 42, Palo Alto Networks). In their threat brief they state that they are actively seeing the vulnerabilities exploited and are working with Microsoft to provide their customers with the latest information and sending breach notifications. The exploitation of CVE-2025-53770 allowed for MFA bypass and secrets theft. Once exploited patching will not remove persistence mechanisms that were put in place by the attackers and full system scans, rotation of cryptographic keys, close monitoring will be required to detect and evict attackers who have gained access to systems. Professional incident response is recommended if you were notified of compromise or if you detect post compromise activity on affected SharePoint servers.
According to Cybernews and a shadowserver dashboard there around 93,000 IP address hosting SharePoint instances are discovered every day "Most of them are in the US (3,043), followed by the Netherlands (541), Ireland (695), the United Kingdom (541), Canada (495), Germany (338), and other countries" (Naprys, Cybernews). Eye Security has notified companies, including "California state, a private energy sector operator in California state, a federal government health org, a private AI tech company, a private Fintech company in New York state, and a state government org in Florida" (Abrams, Bleeping Computer), that the exploit, with the name they have coined as "Toolshell", was used to compromise their systems. Once attackers have access to the SharePoint server they are able to laterally move across the active directory environment especially if the system that was compromised was running both active directory and SharePoint. In the article by Ernestas Naprys a Senior Journalist at Cybernews stated, governments are the most affected followed by software and telecommunications firms based off of a report from Checkpoint Security (Checkpoint).
This attack is not a simple SQL or code injection on an insecure endpoint but it exploits how SharePoint deserializes data on the back end allowing for code to be executed without authentication to the vulnerable system (Lakshmanan, The Hacker News).
Attack Anatomy
- First the attacker will send a POST request to
/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx. - The headder of the request has a referrer of
/_layouts/SignOut.aspxwhich tells the server that they were signed out or are coming from the sign out page. - The data portion of the POST request will send a URL encoded paylaod with the variuble
MSOTlPn_Uri=which contains a matrishka doll of base64 and compressed data that obfuscates a base64 encoded powershell payload. - The powershell payload will do one of three things according to Palo Alto Networks threat breifing
- Iterate through the web.config files on the ASPX server and save them to a debug_dev.js file
- Use w3wp.exe to execute a base64 encoded powershell command that will write an ASPX page to C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx that is designed to steal encryption keys
- The third variation seems to be a spin on the second. The spinstall aspx file is written to ...\15\...\spiinstall.0.aspx instead of ...\16\... it will also rename variubles to single charicters instead of words, and invoke a sleep function at the end of execution.
References: (Unit 42, Palo Alto Networks), (Microsoft Threat Intelligence), (Eye Security)
Threat actors
Linen Typhoon
- Focused on intellectual property theft targeting government, defense, strategic planning, and human rights organizations.
- Known for drive by compromises ( opportunistic sporadic scans )
Violet Typhoon
- Espionage focused targeting former government and military personnel in NGO's, think tanks, higher ed, media outlets, financial and health sectors in the US, Europe and East Asia
- Persistent scanning of specific targets ( targeted attacks )
Storm-2603
- Microsoft states they have a medium confidence that this group is directly related to China
- This threat group has used similar tactics such as scanning for the SharePoint vulnerability and deploying web shells like the previously mentioned threat actors.
- This group has been seen to deploy Warlock and Lockbit ransomware in the past
Sources:
Blue Team Resources
Microsoft's guidance for SharePoint vulnerability CVE-2025-53770 can be found in the link below. The TLDR; a security patch has been released by Microsoft and only affects on premises SharePoint instances and should be applied immediately. Threat hunting indicators also exist in the threat report below. [https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/] (https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/) Additional guidance with more details found in the above link includes:
1. Use supported versions of on-premises SharePoint Server
2. Apply the latest security updates linked above.
3. Deploy Microsoft Defender for Endpoint protection, or equivalent threat solutions
4. Ensure the Antimalware Scan Interface (AMSI) is turned on and configured correctly, with an appropriate antivirus solution such as Defender Antivirus
5. Rotate SharePoint Server ASP.NET machine keys
Indicators of Compromise
Microsoft Provided IOCs
Spinstall0.aspx
- File name
- Web shell used by threat actors Actors have also modified the file name in a variety of ways, such as spinstall.aspx, spinstall1.aspx, spinstall2.aspx
debug_dev.js
- File name of File containing web config data, including MachineKey data
92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- SHA-256 Hash of spinstall0.aspx
c34718cbb4c6.ngrok-free[.]app/file.ps1
- URL Ngrok tunnel delivering PowerShell to C2
\1[5-6]\TEMPLATE\LAYOUTS\debug_dev.js
- File path for stolen web configs
131.226.2[.]6
- Post exploitation C2
134.199.202[.]205
- IP address exploiting SharePoint vulnerabilities
104.238.159[.]149
- IP address exploiting SharePoint vulnerabilities
188.130.206[.]168
- IP address exploiting SharePoint vulnerabilities
Eye Security IOCs
107.191.58[.]76 – first exploit wave
104.238.159[.]149 – second exploit wave
96.9.125[.]147 – shared by PaloAlto Unit42, initial exploit wave
Note: more exploit waves on and after 21th of July: 45.191.66[.]77, 45.77.155[.]170, 64.176.50[.]109, 206.166.251[.]228, 34.72.225[.]196, 34.121.207[.]116, 141.164.60[.]10, 134.199.202[.]205, 188.130.206[.]168
Note: post-exploitation c2 traffic: 131.226.2[.]6
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0 – user agent string used in active exploitation on 18th & 19th of July
Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64;+rv:120.0)+Gecko/20100101+Firefox/120.0 – encoded user agent string for IIS log searches
Note: we will not add any newly observed user agents after 19th of July observation
/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx – POST path used to trigger exploit and push Sharpyshell
/_layouts/16/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx – alternative version
Referer: /_layouts/SignOut.aspx – exact HTTP header used in exploiting ToolPane.aspx
Note: be advised that full URI Referers are also used in the wild: Referer: https://<target>/_layouts/SignOut.aspx and Referer: http://<target>/_layouts/SignOut.aspx
GET request to malicious ASPX file in /_layouts/15/spinstall0.aspx – aspx crypto dumper used by CVE-2021-28474 with tool ysoserial to get RCE on SharePoint
92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514 – SHA256 hash of spinstall0.aspx crypto dumper probably created with Sharpyshell
C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\spinstall0.aspx – location of the malicious aspx file on Windows Servers running SharePoint
Note: alternative paths exists depending on your version: C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\15\TEMPLATE\LAYOUTS\spinstall0.aspx
Note: variants like spinstall.aspx, spinstall1.aspx and spinstall2.aspx, xxx.aspx, 3plx.aspx, debug_dev.js, info.js have also been seen. Be aware that the filename can be anything.
Tactics Techniques and Procedures
- Initial access - Use of known vulnerabilities to exploit internet-facing SharePoint servers
- Execution - PowerShell script execution used to launch payloads
- Persistence - Web shell used to steal machine keys and persist access
- Defense evasion - Payload reflectively loaded via IIS process
- Collection - Web shell used to extract MachineKey data
The Contractors
On July 18th 2025 Reuters published an article stating that the Defense Secretary Pete Hegseth ordered a two week review of the Pentagon's cloud deals. This was prompted by the discovery that Microsoft was using Chinese Engineers for work on cloud computing systems owned and used by the United States Military but were under the supervision of digital escorts who possessed security clearances but not the technical skills to know if what they were doing posed a cybersecurity risk (Nellis, Reuters). This was based off of a ProPublica report on July 15th 2025 that stated Chinese subcontractors who had access to classified systems were often paid starting at $18 per hour (Dudley and Burke, ProPublica).
I like to keep a civil and professional tone when writing these blog posts but this one honestly blows my mind especially due to the fact that Microsoft has been breached by Chinese and Russian state backed groups for years now. Who knows though, they may have been good people with no malicious intent and were technically talented and just happen to be Chinese, people do just live in China and we do not choose where we were born or who our parents are. What rubs me the wrong way is the highly likely possibility that the hiring decision made by Microsoft was based on how much less they could pay the engineers and how many hours they could get the teams over seas to work. The end all is that it does not look good for a company to be hiring from hostile foreign nation states to make a buck over hiring talented and capable people in the United States.
References
(Abrams, Bleeping Computer) Abrams, Lawrence. “Microsoft SharePoint Zero-Day Exploited in RCE Attacks, No Patch Available.” Bleeping Computer, 19 July 2025, www.bleepingcomputer.com/news/microsoft/microsoft-sharepoint-zero-day-exploited-in-rce-attacks-no-patch-available/.
(Checkpoint) Checkpoint Research. “SharePoint Zero-Day CVE-2025-53770 Actively Exploited: What Security Teams Need to Know.” Check Point Research Blog, 21 July 2025, blog.checkpoint.com/research/sharepoint-zero-day-cve-2025-53770-actively-exploited-what-security-teams-need-to-know/.
(CISA Sharepoint) Cybersecurity and Infrastructure Security Agency (CISA). “Update: Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities.” CISA, 20 July 2025, www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities.
(Eye Security) Eye Security Research. “SharePoint Under Siege.” Eye Security, 22 July 2025, research.eye.security/sharepoint-under-siege/.
(Goodin, ArsTechnica) Goodin, Dan. “SharePoint Vulnerability with 9.8 Severity Rating Is under Exploit across the Globe.” Ars Technica, 22 July 2025, arstechnica.com/security/2025/07/sharepoint-vulnerability-with-9-8-severity-rating-is-under-exploit-across-the-globe/.
(Lakshmanan, The Hacker News) Lakshmanan, Ravie. “Critical Microsoft SharePoint Flaw Exploited in the Wild.” The Hacker News, 22 July 2025, thehackernews.com/2025/07/critical-microsoft-sharepoint-flaw.html.
(Microsoft Threat Intelligence) Microsoft Threat Intelligence. “Disrupting Active Exploitation of On-Premises SharePoint Vulnerabilities.” Microsoft Security Blog, 22 July 2025, www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/.
(Naprys, Cybernews) Naprys, Lauryn. “SharePoint Zero-Day Exploitation Threatens Thousands.” Cybernews, 21 July 2025, cybernews.com/security/sharepoint-zero-day-exploitation-threatens-thousands/.
(Unit 42, Palo Alto Networks) Unit 42, Palo Alto Networks. “Microsoft SharePoint CVE-2025-49704, CVE-2025-49706, CVE-2025-53770.” Unit 42 Threat Research, 22 July 2025, unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770/.
Additional Resources
NIST CVE-2025-53770 Detail: https://nvd.nist.gov/vuln/detail/CVE-2025-53770
NIST CVE-2025-49706 Detail: https://nvd.nist.gov/vuln/detail/CVE-2025-49706
NIST CVE-2025-49704 Detail: https://nvd.nist.gov/vuln/detail/CVE-2025-49704
Proof of concept and walkthrough of a payload observed in the wild can be found here: https://isc.sans.edu/diary/32138?n
If you value what is posted here and feel compelled to donate you can do so here. If you are interested in a specific headline or vulnerability and would like a detailed writeup go ahead and get in contact with me directly via the google form found here