
Nefilim Ransomware Group
Written by Nicholas Howland, May 10th 2025
If you value what is posted here and feel compelled to donate you can do so here, no pressure but I would deeply appreciate it.
Preface
I want to preface this with the statement that criminals exist in every country. Note that this cybercriminal group is likely geographically distributed but the actor that was caught just happened to be Ukrainian. It is unclear why Artem was in Spain and the events leading up to his arrest.
Unfortunately most of the links to posts made by companies as advisories that were linked to in the articles broken, as a precautionary measure I have gone ahead and archived each article published by the tech journalist outlets and CTI sources on the Wayback machine. If there are broken links please visit https://web.archive.org/ and copy and paste the URL to the page in the search bar and the most recently archived article will appear.
Lastly, if you think I am talking about your company specifically, I am not poor security practices are way more common than you think which is why Ransomware and Data Breaches are not isolated uncommon events.
If you want the response chat GPT gave me when asked to generate a report about Nefilim prior to me posting this article it can be found here: https://exylum.tech/blog/gpt-threat-actor-25-05.html.
The Actor
Artem Stryzhak was arrested in Spain and extradited to the United States for fraud and conspiracy in relation to the Ransomware group Nefilim. Nefilim has not been active since 2021, but when they were active they carried out ransomware operations against high-revenue organizations in the US, France, Germany, the Netherlands, Norway, Switzerland, Canada, and Australia DOJ (2025), "Indictment Document". According to an additional press release from the Department of Justice Artem was convinced by a Nefilim administrator to target companies with more than $200 million in annual revenue in these countries DOJ (2025), "Press Release: Ukrainian National Extradited to Spain".
TLDR
- Living off the Lan bins are used for lateral movement and the third party tool MEGASync was used to exfiltrate data.
- Cobalt Strike was used to push scripts and upload executables to encrypt, compress, and exfiltrate files.
- The Nefilim group has been active since late 2019 to 2021 around the same time that the Nemty ransomware family went private.
- A number of attacks targeted Citrix appliances using CVE-2019-11634 and CVE-2019-19781.
- Exposed RDP servers were also used to gain initial access by brute forcing login credentials.
- Tools used in their attacks included; Mimikatz, LaZagne, NirSoft’s NetPass, PSExec, and WIMC
- Patch systems, Dont allow excessive administrative permissions, monitor for file centralization and compression, monitor antivirus status.
Indictment

The following comes from the indictment which can be found here. Note that the dates are approximate as stated in the indictment.
Key Points
- There were around 5 conspirators mentioned in the indictment.
- The group would first gain access to the networks, exfiltrate, and then extort the victims by threatening to leak documents, this is known as hack and leak extortion.
- The group would tell new co-conspirators that they were targeting targets inside of the United States, Canada or Australia with more than $100 Million in annual revenue. Artem was tasked with targeting companies inside of the United States Canada and Australia with annual revenues above $200 million after approximately 9 months of involvement.
- Used otherwise legitimate tools, such as Cobalt Strike and WinSCP, to push code remotely in order to exfiltrate and encrypt files.
- Email addresses and ransom notes were baked into executables which were customized per victim.
- Targeted industries such as aviation, engineering, chemicals, eyewear, insurance, construction, energy and pet care. However annual revenue was what the actors were targeting not industry, indicating financially motivated criminality.
- Targets were chosen by using information sourced from Business Databases, similar to if not including ZoomInfo which is reportedly popular amongst ransomware actors BleepingComputer (2025), "Ukrainian Extradited to US for Nefilim Ransomware Attacks".
- Information from business databases was also used to preform reconnaissance on companies such as finding names of key people for additional reconnaissance [implied].
- Victims who paid typically received the decryption key but if payments were not made then files were leaked on "Corporate Leaks" sites.
- The timeline of "overt acts" ranges from September 2020 to October 2021
Timeline
- September 2020, Artem used a virtual private server to access an instant messaging platform where communications with co-conspirators took place and computers in Victim 4's company had files encrypted and a ransom was demanded but not paid.
- October 2020, Victim 4's 102GB of files were released on the "Corporate Leaks" sites after not paying the ransom.
- June 2021, Victim 5 was targeted and files were encrypted. Artem agreed to become a Nefilim Affiliate. Artem was given access to the Nefilim administrative panel. Victim 7's network was accessed by Artem and WinSCP was used to exfiltrate files relating to Oil, Gas, and Transportation. Another co-conspirator was able to extort a ransom payment from Victim 5. Artem created three email accounts to serve as points of contact for Nefilim in the ransom notes, these email addresses were baked into the executable files which were customized for each victim.
- July 2021, Artem agreed to target companies in the United States Canada and Australia with annual revenues above $200 million. Nefilim attempted to access several companies including Victim 8, within five hours of gaining access to victim 8 access to computers was attempted.
- August 2021, an individual approaches the Nefilim group hoping to assist them, Nefilim states that they are interested in targets within the United States, Canada or Australia with more than $100 Million in annual revenue. Another co-conspirator provided 21 email accounts and associated passwords for use in ransom negotiations. 9 email addresses were provided to two of the other co-conspirators, three of which were baked into custom executable scripts by one of the co-conspirators.
- September to October 2021, An un-named researcher used public tracing tools to follow the cryptocurrency transactions from the payment made by Victim 5 to their destination wallets.
- October 2021, Data from Victim 6 was downloaded and files were encrypted with three of the nine emails provided to co-conspirators in October 2021. Note that three email addresses were provided per executable which potentially means that there were three co-conspirators responsible for communicating with the victim. Late October Victim 6 contacted Nefilim confirming that they had received the ransom demand and requested proof of data exfiltration after which Nefilim demanded 23.5 BTC valued at approximately 1.5 Million dollars.
Victims
Based on the indictment and a reports from Qualys and Trend Micro, the victims are linked by the total revenue of $100 to $200 Million and some had unpatched Citrix gateway application servers.
In the indictment the victims are listed in the following order:
- An engineering consulting company located in France
- A company in the Aviation Industry located in Eastern District of New York
- A chemical company located in the Southern District of Ohio
- An international eyewear company located in the Eastern District of New York
- An insurance company located in the Central District of Illinois
- A company in the construction industry in the Western District of Texas
- A company in the oil, gas, and transportation Industry
- A company in the pet care industry located in the Eastern District of Missouri
Piecing Things Together

Luxottica suffered a ransomware event around September 21st and had to hault computer operations. The attack was possible due to an unpatched vulnerability linked to CVE-2019-19781 in Citrix servers (Bit Defender). The CVE scores as a 9.8 Critical and is listed in CISA's known exploited vulnerabilities catalogue. The CVE allows for directory traversal and remote code execution. A full writeup of what was documented is available from CISA (2025), "CVE-2019-19781 Cybersecurity Advisory" and mitigations were posted by Citrix and last modified on September 1st 2021 Citrix (2025), "Mitigation Steps for CVE-2019-19781".
The article by Bit Defender included a statement that the company did not suspect data exfiltration had taken place. In another article by Bleeping Computer, a Luxottica security employee based out of Italy made a statement on approximately the 23rd of September, 2020 that no data was stolen in a LinkedIn post "a) There is currently no access or theft of information from users and consumers. b) Once the event was analyzed, the clues were collected in less than 24 hours and the procedure for cleaning up the affected servers began. Work activities are gradually returning to normal in the #Milano plants and headquarters." The indictment indicates that Luxicota aka Victim 4 had around 102GB of data published after refusing to pay the ransom in October 2020. You know what they say about assumptions... gald they didn't pay the ransom though!
Orange, one of the largest mobile companies in France, was the victim of "A crypto virus-type computer attack" on July 4th 2020. There is no information publicly available, released from the company or their security provider, about what the initial access techniques were or indicators of compromise. BleepingComputer (2025), "Orange Confirms Ransomware Attack Exposing Business Customers Data" Bitdefender (2025), "Orange Confirms Ransomware Attack Compromising Data of Business Solutions Customers"
Another European company, A subsidiary of the Dussman Group, DKA cooling specialist Dresdner Kühlanlagenbau GmbH was a victem of Nefilim as well. Their security provider Bad Packets ruled out a vulnerability in the VPN gateways according to a ZDNET article ZDNet (2025), "Ransomware-Angriff auf Dussmann: Hacker veröffentlichen Daten". Once again there is not a lot of information about how DKA was initially compromised or indicators of compromise relating to the attack.
The website for the company Bad Packets has gone offline after they were acquired by Okta in Febuary 2023. Bad Packets operates a honeypot network which allows Okta to gain insights to provide their identity platform with better detection capabilities for false logins and threat actor activity.
Toll Group, a freight and delivery service company based out of Australia, took down its IT systems after detecting unusual activity in their network around May 6th 2020. Later on reporting from Recorded Future has a quote from Allan Liska who stated "The actors behind Nefilim primarily gain access through vulnerable RDP servers, though there are unverified reports of them expanding their attack repertoire, ... This is a pretty common development path for new ransomware actors: They start with open or vulnerable RDP servers and then expand to other attack methods." This was the second ransomware attack against the Toll Group was faced with in 2020 and in that single breach the company had 220GB of data stolen Threatpost (2025), "Ransomware Attack on Toll Group".
Whirlpool was breached but there is very little information regarding the breach and indicators of compromise other than their data was published on "Corporate Leaks" site Bitdefender (2025), "Nefilim Hits Whirlpool with Ransomware, Publishes Some Stolen Data". In an article by Forbes Aban Offshore Limited an oil and gas company was also the target of Nefilim (Forbes, Whirlpool).
Nefilim Ransomware Family

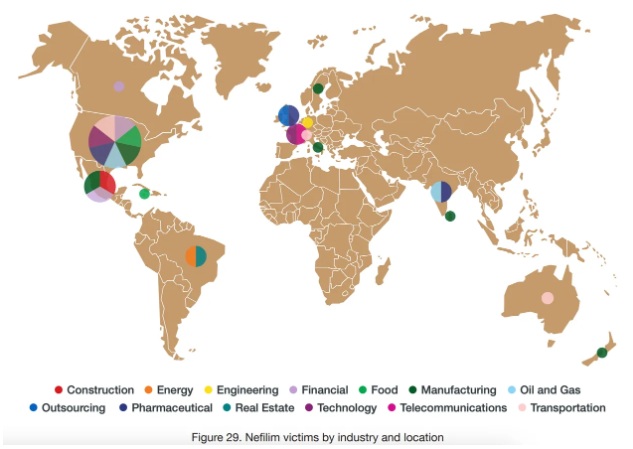
The following infographic shows the geographic location distribution of companies attacked with color coding by industry courtesy from the Trend Micro Report which can be found in the references.
Some of the first reporting comes from Bleeping computer in March of 2020. The article points out that the Nefilim shares much of the same code as a predecessor Nemty. Nefilim became active around February 2020 BleepingComputer (2025), "New Nefilim Ransomware Threatens to Release Victims' Data". The Sentinel One Report mentioned in the Bleeping Computer article, states that Nefilim shares much of the same code as Nemty another Ransomware family.
Nefilim emerged in March 2020 and Nemty appeared/launched in August of 2019 as a public affiliate program, meaning that invites were not required to become involved with the ransomware group. The two differ in the fact that Nefilim requires victims to send an email to an address in the ransom note in order to arrange payment where as Nemty directs victims to a TOR based payment portal. There are differing artifacts, such as strings, left in encrypted files as well SentinelOne (2025) "Meet Nemty’s Successor: Nephilim Ransomware". On April 15th 2020, Bleeping Computer reported that Nemty took its operations private after operating since the summer of 2019 publicly BleepingComputer (2025), "Nemty Ransomware Shuts Down Public RaaS Operation, Goes Private".
Nefilim uses AES-128 to encrypt files and RSA-2048 to encrypt the private key of the AES encrypted files. Nemty was seen to have been using RSA-1028 and AES-128 in counter mode, an extension onto a block mode encryption scheme https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Galois/counter_(GCM). Post infection files are given the file extension .nefilim or .NEFILIM.
Findings from a Qualys Report indicate the following. Nefilim favored two vulnerabilities that existed in Citrix gateway devices CVE-2019-11634 and CVE-2019-19781. Ransomware was delivered through exposed RDP services and that login credentials were brute forced. Living off the Land binaries used to execute .bat scripts on remote computers were psexec and WIMC. The bat file would stop processes and disable various services relating to logging, antivirus, backup processes. Data exfiltration occurred by copying data from servers to a compromised device compressing them using a dropped 7zip binary and using Mega Sync to exfiltrate the data Qualys (2025), "Nefilim Ransomware Report".
Trend Micro also published a threat report on Nefilim in February of 2021. The threat report also names CVE-2019-19781 being used to target Citrix systems as well as utilizing exposed RDP services and brute forcing logins being for initial access. Credential gathering tools that were used for lateral movement included Mimikatz, LaZagne, and NirSoft’s NetPass.
Lateral movement activities included using PSExec and built in utilities such as WIMC. Data was consolidated from systems in the network using file shares then compressed with 7zip after which MEGAsync was used to exfiltrate the compressed data.
Sophos also published a blog post detailing how their Rapid Response team handled the incident which impacted more than 100 systems. Unfortunately the client had not purchased one of their products which would have effectively stopped the attack and their clients files were encrypted but the Sophos Rapid Response Team came in and responded rapidly.
The report from Sophos goes on to state that their client had an instance of "Citrix Storefront 7.15 CU3 was vulnerable at time of incident to 1 Critical (CVE-2019-11634) and 4 High rated CVE vulnerabilities (CVE-2019-13608, CVE-2020-8269, CVE-2020-8270, CVE-2020-8283)." Nefilim also used RDP logins to maintain access to systems and used MimiKatz to extract credentials. The only new piece of information was that Nefilim had leveraged an account that was part of the Domain Administrator user group, based off of the tone of the report it did not sound like their job functions required the use of a domain administrator, and quoted Mackenzie “People assume because a person is an executive or is in charge of the network that they need to be using a domain admin account. This isn’t true and it’s dangerous.” Once the attacker gained access to a domain administrator account, they then created a new administrative account which was then used to delete 150 virtual servers and bitlocker encrypt the servers backups. Heller, M. (2021, January 26) "Nefilim ransomware attack uses “ghost” credentials"
PSExec was used in lateral movement to execute scrips on systems within the network, it is commonly used as a remote administration tool but is not built into windows by default. WMI was used as well for lateral movement, but unlike PSExec it is built into windows and enabled by default prior to January 2024 Microsoft (2025), "WMIC Deprecation: Next Steps".
Recommendations
- Disable RDP if it is not used. If required change RDP port to a non-standard port.
- Keep strong and unique passwords for login accounts especially for public facing and remote access services.
- Require RDP to be accessible only from a VPN that has strong credentials and requires multi factor authentication if possible.
- Check on backup status and maintain backups.
- Use a combination of offline and online backups.
- Patch or GTFO (Get Them Firewalled or Offline)
- Do not allow the use of cracked or pirated software on corporate systems.
- Monitor for lateral movement such as internal network scanning, file transfers at odd times, and strange logins.
- Only grant the access permissions needed for a specific task or role and disable accounts that are no longer used, when setting up automation that requires higher level privileges be sure to have a new account made and not use an existing user account.
MITRE ATT&CK TTPs
- T1593.02 - Search Open Websites/Domains - Utilized business databases to gather information about targets - https://attack.mitre.org/techniques/T1593/
- T1592.02 - Gather Victim Host Information: Software - Discovered vulnerable Citrix gateways and exploited them - https://attack.mitre.org/techniques/T1592/002/
- T1190 - Exploit Public-Facing Application - Exploited exposed RDP services and Citrix gateways - https://attack.mitre.org/techniques/T1190/
- T1078.02 - Valid Accounts: Domain Accounts - Obtained Domain administrator credentials - https://attack.mitre.org/techniques/T1078/002/
- T1059.03 - Command and Scripting Interpreter: Windows Command Shell - Use of .bat scripts and Windows Command Shell commands pushed through psexec - https://attack.mitre.org/techniques/T1059/003/
- T1136.02 - Create Account: Domain Account - Created valid Domain Administrator account to delete servers and encrypt backups - https://attack.mitre.org/techniques/T1136/002/
- T1133 - External Remote Services - Brute forced RDP credentials - https://attack.mitre.org/techniques/T1133/
- T1562.002 - Impair Defenses: Disable Windows Event Logging - Disabled Event logging from the Qualys report - https://attack.mitre.org/techniques/T1562/002/
- T1562.001 - Impair Defenses: Disable or Modify Tools - Disabled security processes and backups Qualys report - https://attack.mitre.org/techniques/T1562/001/
- T1555 - Credentials from Password Stores - Use of Mimikatz, LaZagne, and Nirsoft, to gather credentials - https://attack.mitre.org/techniques/T1555/
- T1210 - Exploitation of Remote Services - Lateral movement inside of the network using RDP - https://attack.mitre.org/techniques/T1210/
- T1074 - Data Staged - Use of file sharing to centralize data for archival and export - https://attack.mitre.org/techniques/T1074/
- T1560 - Archive Collected Data: Archive via Utility - Use of 7zip to archive collected data - https://attack.mitre.org/techniques/T1560/001/
- T1048 - Exfiltration Over Alternative Protocol - Use of Megasync to exfiltrate files - https://attack.mitre.org/techniques/T1048/
- T1486 - Data Encrypted for Impact - Files encrypted for ransom - https://attack.mitre.org/techniques/T1486/
References
- Bitdefender. (2025). Orange Confirms Ransomware Attack Compromising Data of Business Solutions Customers. www.bitdefender.com. Link
- Bitdefender. (2025). Nefilim Hits Whirlpool with Ransomware, Publishes Some Stolen Data. www.bitdefender.com. Link
- Bitdefender. (2025). Hackers Stole 220GB of Data in Toll Group Ransomware Attack. www.bitdefender.com. Link
- Bitdefender. (2025). Eyewear Giant Luxottica Confirms Ransomware Attack. www.bitdefender.com. Link
- BleepingComputer. (2025). Ukrainian Extradited to US for Nefilim Ransomware Attacks. www.bleepingcomputer.com. Link
- BleepingComputer. (2025). Orange Confirms Ransomware Attack Exposing Business Customers Data. www.bleepingcomputer.com. Link
- BleepingComputer. (2025). Ray-Ban Owner Luxottica Confirms Ransomware Attack, Work Disrupted. www.bleepingcomputer.com. Link
- BleepingComputer. (2025). Business Giant Dussmann Group's Data Leaked After Ransomware Attack. www.bleepingcomputer.com. Link
- BleepingComputer. (2025). New Nefilim Ransomware Threatens to Release Victims' Data. www.bleepingcomputer.com. Link
- BleepingComputer. (2025). Nemty Ransomware Shuts Down Public RaaS Operation, Goes Private. www.bleepingcomputer.com. Link
- CISA. (2025). CVE-2019-19781 Cybersecurity Advisory. www.cisa.gov. Link
- Citrix. (2025). Mitigation Steps for CVE-2019-19781. support.citrix.com. Link
- DOJ. (2025). Indictment Document. www.justice.gov. Link
- DOJ. (2025). Press Release: Ukrainian National Extradited to Spain. www.justice.gov. Link
- Microsoft. (2025). WMIC Deprecation: Next Steps. techcommunity.microsoft.com. Link
- Qualys. (2025). Nefilim Ransomware Report. blog.qualys.com. Link
- Recorded Future. (2025). Nefilim Ransomware Extradited to Spain. therecord.media. Link
- SentinelOne. (2025). Meet Nemty’s Successor: Nephilim Ransomware. www.sentinelone.com. Link
- SecurityWeek. (2025). Ukrainian Nefilim Ransomware Affiliate Extradited to US. www.securityweek.com. Link
- Heller, M. (2021, January 26). Nefilim ransomware attack uses “ghost” credentials. Sophos News. Link
- Trend Micro. (2025). Modern Ransomware’s Double Extortion Tactics. www.trendmicro.com. Link
- Threatpost. (2025). Ransomware Attack on Toll Group. threatpost.com. Link
- ZDNet. (2025). A Deep Dive into Nefilim. www.zdnet.com. Link
- ZDNet. (2020). Ransomware-Angriff auf Dussmann: Hacker veröffentlichen Daten. www.zdnet.de. Link
Indicators of Compromise and Rules
I didn't find very many useful IOC GitHub repositories other than the Sophos one.
Windows defender has Nefilim catalogued Ransom:Win32/Nefilim.GM!MTB https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Ransom:Win32/Nefilim.GM!MTB&ThreatID=2147754444
SHA256 Detection name
08c7dfde13ade4b13350ae290616d7c2f4a87cbeac9a3886e90a175ee40fb641 Ransom.Win32.NEFILIM.A
205ddcd3469193139e4b93c8f76ed6bdbbf5108e7bcd51b48753c22ee6202765 Ransom.Win32.NEFILIM.D
5da71f76b9caea411658b43370af339ca20d419670c755b9c1bfc263b78f07f1 Ransom.Win32.NEFILIM.D
7a73032ece59af3316c4a64490344ee111e4cb06aaf00b4a96c10adfdd655599 Ransom.Win32.NEFILIM.C
eacbf729bb96cf2eddac62806a555309d08a705f6084dd98c7cf93503927c34f Ransom.Win32.NEFILIM.G
ee9ea85d37aa3a6bdc49a6edf39403d041f2155d724bd0659e6884746ea3a250 Trojan.Win64.NEFILIM.A
f51f128bca4dc6b0aa2355907998758a2e3ac808f14c30eb0b0902f71b04e3d5 Ransom.Win32.NEFILIM.D
fdaefa45c8679a161c6590b8f5bb735c12c9768172f81c930bb68c93a53002f7 Ransom.Win32.NEFILIM.D
Sentinal One: https://www.sentinelone.com/labs/meet-nemty-successor-nefilim-nephilim-ransomware/
SHA256
8be1c54a1a4d07c84b7454e789a26f04a30ca09933b41475423167e232abea2b
b8066b7ec376bc5928d78693d236dbf47414571df05f818a43fb5f52136e8f2e
3080b45bab3f804a297ec6d8f407ae762782fa092164f8ed4e106b1ee7e24953
7de8ca88e240fb905fc2e8fd5db6c5af82d8e21556f0ae36d055f623128c3377
b227fa0485e34511627a8a4a7d3f1abb6231517be62d022916273b7a51b80a17
3bac058dbea51f52ce154fed0325fd835f35c1cd521462ce048b41c9b099e1e5
353ee5805bc5c7a98fb5d522b15743055484dc47144535628d102a4098532cd5
5ab834f599c6ad35fcd0a168d93c52c399c6de7d1c20f33e25cb1fdb25aec9c6
52e25bdd600695cfed0d4ee3aca4f121bfebf0de889593e6ba06282845cf39ea
35a0bced28fd345f3ebfb37b6f9a20cc3ab36ab168e079498f3adb25b41e156f
7a73032ece59af3316c4a64490344ee111e4cb06aaf00b4a96c10adfdd655599
08c7dfde13ade4b13350ae290616d7c2f4a87cbeac9a3886e90a175ee40fb641
D4492a9eb36f87a9b3156b59052ebaf10e264d5d1ce4c015a6b0d205614e58e3
B8066b7ec376bc5928d78693d236dbf47414571df05f818a43fb5f52136e8f2e
fcc2921020690a58c60eba35df885e575669e9803212f7791d7e1956f9bf8020
SHA1
4595cdd47b63a4ae256ed22590311f388bc7a2d8
1f594456d88591d3a88e1cdd4e93c6c4e59b746c
6c9ae388fa5d723a458de0d2bea3eb63bc921af7
9770fb41be1af0e8c9e1a69b8f92f2a3a5ca9b1a
e99460b4e8759909d3bd4e385d7e3f9b67aa1242
e53d4b589f5c5ef6afd23299550f70c69bc2fe1c
c61f2cdb0faf31120e33e023b7b923b01bc97fbf
0d339d08a546591aab246f3cf799f3e2aaee3889
bbcb2354ef001f476025635741a6caa00818cbe7
2483dc7273b8004ecc0403fbb25d8972470c4ee4
d87847810db8af546698e47653452dcd089c113e
E94089137a41fd95c790f88cc9b57c2b4d5625ba
Bd59d7c734ca2f9cbaf7f12bc851f7dce94955d4
f246984193c927414e543d936d1fb643a2dff77b
d87847810db8af546698e47653452dcd089c113e
Sophos: https://github.com/sophoslabs/IoCs/blob/master/Ransomware-Netfilim.csv
Indicator_type Data Note
sha256 e7ccbcc9f500272f8b6422e9900c5131768cc9ca074e6cb8cc92bce385a7ee2e Netfilim (Nemty) ransomware
sha256 3cd9b8f675d4718c4d73a9b1656836790a058b8ba46c1e0f254d46775ab06556 Cobalt Strike
command_line_parameter -nop -w hidden -c IEX ((new-object net.webclient).downloadstring Powershell command
domain aes.one C2
file_path_name %AppData%/Local/MEGAsync.exe MEGA app to exfiltrate data
file_path_name %AppData%/Local/MEGAupdater.exe MEGA app to exfiltrate data
ip 45.11.180.250 Threat Actor Infrastructure
filename INFECTION-HELP.txt Ransom Note
Yara rules because we love them, yep used ChatGPT to generate it:
rule Nefilim
{
meta:
description = "Detects Nefilim (Netfilim) ransomware samples"
author = "ChatGPT"
date = "2025-05-10"
reference1 = "Microsoft: Ransom:Win32/Nefilim.GM!MTB"
reference2 = "Sophos IoCs: https://github.com/sophoslabs/IoCs"
reference3 = "SentinelOne: https://www.sentinelone.com/labs/meet-nemty-successor-nefilim-nephilim-ransomware/"
sha256_01 = "8be1c54a1a4d07c84b7454e789a26f04a30ca09933b41475423167e232abea2b"
sha256_02 = "b8066b7ec376bc5928d78693d236dbf47414571df05f818a43fb5f52136e8f2e"
sha256_03 = "3080b45bab3f804a297ec6d8f407ae762782fa092164f8ed4e106b1ee7e24953"
sha256_04 = "7de8ca88e240fb905fc2e8fd5db6c5af82d8e21556f0ae36d055f623128c3377"
sha256_05 = "b227fa0485e34511627a8a4a7d3f1abb6231517be62d022916273b7a51b80a17"
sha256_06 = "3bac058dbea51f52ce154fed0325fd835f35c1cd521462ce048b41c9b099e1e5"
sha256_07 = "353ee5805bc5c7a98fb5d522b15743055484dc47144535628d102a4098532cd5"
sha256_08 = "5ab834f599c6ad35fcd0a168d93c52c399c6de7d1c20f33e25cb1fdb25aec9c6"
sha256_09 = "52e25bdd600695cfed0d4ee3aca4f121bfebf0de889593e6ba06282845cf39ea"
sha256_10 = "35a0bced28fd345f3ebfb37b6f9a20cc3ab36ab168e079498f3adb25b41e156f"
sha256_11 = "7a73032ece59af3316c4a64490344ee111e4cb06aaf00b4a96c10adfdd655599"
sha256_12 = "08c7dfde13ade4b13350ae290616d7c2f4a87cbeac9a3886e90a175ee40fb641"
sha256_13 = "d4492a9eb36f87a9b3156b59052ebaf10e264d5d1ce4c015a6b0d205614e58e3"
sha256_14 = "fcc2921020690a58c60eba35df885e575669e9803212f7791d7e1956f9bf8020"
sha256_15 = "205ddcd3469193139e4b93c8f76ed6bdbbf5108e7bcd51b48753c22ee6202765"
sha256_16 = "5da71f76b9caea411658b43370af339ca20d419670c755b9c1bfc263b78f07f1"
sha256_17 = "eacbf729bb96cf2eddac62806a555309d08a705f6084dd98c7cf93503927c34f"
sha256_18 = "ee9ea85d37aa3a6bdc49a6edf39403d041f2155d724bd0659e6884746ea3a250"
sha256_19 = "f51f128bca4dc6b0aa2355907998758a2e3ac808f14c30eb0b0902f71b04e3d5"
sha256_20 = "fdaefa45c8679a161c6590b8f5bb735c12c9768172f81c930bb68c93a53002f7"
sha1_01 = "4595cdd47b63a4ae256ed22590311f388bc7a2d8"
sha1_02 = "1f594456d88591d3a88e1cdd4e93c6c4e59b746c"
sha1_03 = "6c9ae388fa5d723a458de0d2bea3eb63bc921af7"
sha1_04 = "9770fb41be1af0e8c9e1a69b8f92f2a3a5ca9b1a"
sha1_05 = "e99460b4e8759909d3bd4e385d7e3f9b67aa1242"
sha1_06 = "e53d4b589f5c5ef6afd23299550f70c69bc2fe1c"
sha1_07 = "c61f2cdb0faf31120e33e023b7b923b01bc97fbf"
sha1_08 = "0d339d08a546591aab246f3cf799f3e2aaee3889"
sha1_09 = "bbcb2354ef001f476025635741a6caa00818cbe7"
sha1_10 = "2483dc7273b8004ecc0403fbb25d8972470c4ee4"
sha1_11 = "d87847810db8af546698e47653452dcd089c113e"
sha1_12 = "e94089137a41fd95c790f88cc9b57c2b4d5625ba"
sha1_13 = "bd59d7c734ca2f9cbaf7f12bc851f7dce94955d4"
sha1_14 = "f246984193c927414e543d936d1fb643a2dff77b"
strings:
$ransom_note = "INFECTION-HELP.txt"
$ps_command = "-nop -w hidden -c IEX ((new-object net.webclient).downloadstring" nocase
$mega1 = "MEGAsync.exe"
$mega2 = "MEGAupdater.exe"
$domain = "aes.one"
$ip = "45.11.180.250"
condition:
any of ($ransom_note, $ps_command, $mega1, $mega2, $domain, $ip)
}
And the surrocata ruleset also GPT generated:
alert http any any -> any any (
msg:"Nefilim Ransomware - Suspicious PowerShell Downloadstring Command";
content:"-nop"; http_uri;
content:"hidden"; http_uri;
content:"downloadstring"; http_uri;
nocase;
classtype:trojan-activity;
reference:url,github.com/sophoslabs/IoCs/blob/master/Ransomware-Netfilim.csv;
sid:4000001;
rev:1;
)
alert http any any -> any any (
msg:"Nefilim Ransomware - MEGA used for exfiltration (MEGAsync.exe)";
content:"MEGAsync.exe"; http_uri;
nocase;
classtype:exfiltration;
sid:4000002;
rev:1;
)
alert http any any -> any any (
msg:"Nefilim Ransomware - MEGA used for exfiltration (MEGAupdater.exe)";
content:"MEGAupdater.exe"; http_uri;
nocase;
classtype:exfiltration;
sid:4000003;
rev:1;
)
alert dns any any -> any any (
msg:"Nefilim Ransomware - Known C2 Domain";
content:"aes.one"; nocase;
classtype:trojan-activity;
sid:4000004;
rev:1;
)
alert ip any any -> 45.11.180.250 any (
msg:"Nefilim Ransomware - Known C2 IP";
classtype:trojan-activity;
sid:4000005;
rev:1;
)
alert http any any -> any any (
msg:"Nefilim Ransomware - Ransom Note Access";
content:"INFECTION-HELP.txt"; http_uri;
nocase;
classtype:attempted-user;
sid:4000006;
rev:1;
)
And finally Sigma rules just for fun, also GPT generated
nefilim_powershell.yml
title: Suspicious PowerShell DownloadString Activity - Nefilim
id: 8fd5e6ae-490b-4a1b-a223-8ea870c70d4a
status: stable
description: Detects obfuscated PowerShell command associated with Nefilim ransomware
author: OpenAI ChatGPT
date: 2025/05/10
logsource:
product: windows
service: powershell
detection:
selection:
EventID: 4104
ScriptBlockText|contains:
- "-nop"
- "hidden"
- "IEX"
- "downloadstring"
condition: selection
fields:
- ComputerName
- UserId
- ScriptBlockText
level: high
tags:
- attack.execution
- attack.t1059.001
- nefilim
nefilim_megasync.yml
title: MEGA Exfiltration Tool Execution - Nefilim
id: 192a5dd2-3d17-464f-85be-e7067bc92aa0
status: stable
description: Detects execution of MEGA tools abused by Nefilim ransomware for exfiltration
author: OpenAI ChatGPT
date: 2025/05/10
logsource:
product: windows
service: sysmon
detection:
selection:
EventID: 1
Image|endswith:
- '\\MEGAsync.exe'
- '\\MEGAupdater.exe'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
level: medium
tags:
- attack.exfiltration
- nefilim
nefilim_ransomnote.yml
title: Ransom Note File Creation - Nefilim
id: f885b255-caa7-43f9-83d5-62e4adfdf008
status: stable
description: Detects the creation of a ransom note file known to be dropped by Nefilim ransomware
author: OpenAI ChatGPT
date: 2025/05/10
logsource:
product: windows
service: sysmon
detection:
selection:
EventID: 11
TargetFilename|endswith: 'INFECTION-HELP.txt'
condition: selection
fields:
- Image
- TargetFilename
level: high
tags:
- attack.impact
- ransomware
- nefilim
nefilim_dns.yml
title: DNS Query to Known Nefilim C2 Domain
id: a7f314b3-91fc-42e7-a1b3-8930dd6bd8c3
status: stable
description: Detects DNS resolution attempts to a known Nefilim command and control domain
author: OpenAI ChatGPT
date: 2025/05/10
logsource:
product: windows
service: dns-server
detection:
selection:
QueryName|endswith: "aes.one"
condition: selection
fields:
- QueryName
- ProcessName
level: high
tags:
- attack.command_and_control
- nefilim